Hijacking DOMAIN
The domain hijacking is a form a little out of the mainstream because
it would be a little more focused on social engineering because it is
part of an attack directed at a specific victim in this case would be
the original person and owner of the domain is that victim who owns the
email that made the registration, the email I buy the domain # Epico
since in certain forms intervene an email is much easier to make the
intrusion itself to this website for brute force tools abound, phishing,
email cracking or just send an email and wait wing victim to open it
using a little social engineering we are talking about 65% in each wing
victim sending mail. Well for that we must understand that in the hijacking DOMAIN two things only start the DNS and hosting.
Which means each and everyone must know both the hosting and DNS has
its own panel but where would we focus on specifically PANEL which can
handle DNS routing services.
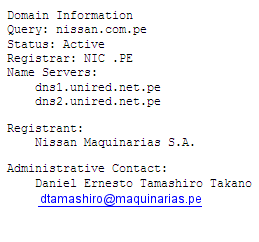
Now go back to the attack of linking to domain hijacking first thing we have is the access panel for it having DNS information:
> The name of the domain that will make the kidnapping.
> The email address to which the record was made of the domain.
This useful information is very easy to get what we can do with a
domain whois domain the victim and we introduce a simple enter and begin
the search for information about the domain in which we are performing
the attack once it finishes loading the data we WHOIS RECORD is where
e-mail, provided by XXX company registration, ETC.
Once you take control over this information and taking into account the
administrative mail DNS service proceeds to intervene once made the
account headed domain provider and we click on the and automatically sends us link to reset your password to
enter the DNS PANEL clear this was done after the intervention to that
email and in it we would realize only a redirect page if not all domains
registered to that email account. # END # 1